chat
Toasting, Chatting, or Deejaying is the act of
talking or chanting over a rhythm or
beat. The lyrics can be
both improvised or pre-written. Toasting has been used in various African
traditions, such as griots chanting over a drum beat,
Jamaican music forms, such as dancehall, reggae,
ska, dub, and lovers rock. Toasting's mix of talking
and chanting may have
influenced the development of rapping in US hip hop music. The combination of singing and toasting is known as singjaying.
Overview
Instant messaging (IM) and chat are technologies that facilitate near real-time text based communication between two or more participants over a network. It is important to understand that what separates chat and instant messaging from technologies such as e-mail is the perceived synchronicity of the communication by the user - Chat happens in real-time before your eyes. For this reason, some people consider communication via instant messaging to be less intrusive than communication via phone. However, some systems allow the sending of messages to people not currently logged on (offline messages), thus removing much of the difference between Instant Messaging and e-mail.
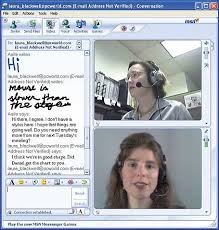
Instant Messaging allows instantaneous communication between a number of parties simultaneously, by transmitting information quickly. Some IM systems allow users to use webcams and Microphone which made them more popular than others. Due to this feature users can have a real-time conversation. In addition IM has additional features such as: the immediate receipt of acknowledgment or reply, group chatting, conference services (including voice and video), conversation logging and file transfer.
IM allows effective and efficient communication, featuring immediate receipt of acknowledgment or reply. In certain cases Instant Messaging involves additional features, which make it even more popular, i.e. to see the other party, e.g. by using web-cams, or to talk directly for free over the Internet.
It is possible to save a conversation for later reference. Instant messages are typically logged in a local message history which closes the gap to the persistent nature of e-mails and facilitates quick exchange of information like URLs or document snippets (which can be unwieldy when communicated via telephone).
IM Language
Users mostly abbreviate common words or expressions to quicken conversations or to omit keystrokes. It is also referred to as internet slang or text speak in text messaging. See Internet slang appendix for examples.
Security and archiving
In the early 2000s, a new class of IT security provider emerged to provide remedies for the risks and liabilities faced by corporations who chose to use IM for business communications. The IM security providers created new products to be installed in corporate networks for the purpose of archiving, content-scanning, and security-scanning IM traffic moving in and out of the corporation. Similar to the e-mail filtering vendors, the IM security providers focus on the risks and liabilities described above.
class of IT security provider emerged to provide remedies for the risks and liabilities faced by corporations who chose to use IM for business communications. The IM security providers created new products to be installed in corporate networks for the purpose of archiving, content-scanning, and security-scanning IM traffic moving in and out of the corporation. Similar to the e-mail filtering vendors, the IM security providers focus on the risks and liabilities described above.
With rapid adoption of IM in the workplace, demand for IM security products began to grow in the mid-2000s. By 2007, the preferred platform for the purchase of security software had become the "appliance", according to IDC, who estimate that by 2008, 80% of network security products will be delivered via an appliance
Risks and liabilities
Employees may misuse the instant messaging client to communicate on a personal level with friends and family. This is poor use of a business’s time and resources, as the employee’s effectiveness will most certainly decrease due to the added distractions. This is hard to control as it is almost impossible constrain the types of messages sent, or who they are sent too. Licari, J. (2005, May).
Within the company there is also the risk of employees use instant message to release confidential information and project details to an outside source. This is an issue that is difficult to control, although the way to control it is to enforce an IM policy with well defined rules such us: don’t release important information to an outside source, don’t talk with your relatives for more than ten minutes a day and don’t accept files from unknown sources. After the implementation of this policy archiving should be carry out, in order to make shore that any conversation within the company is safe for secure proposes.
Although instant messaging delivers many benefits, it also carries with it certain risks and liabilities, particularly when used in workplaces. Among these risks and liabilities are:
Security risks (e.g. IM used to infect computers with spyware, viruses, trojans, worms)
Compliance risks
Inappropriate use
Intellectual property leakage
Crackers (malicious "hacker" or black hat hacker) have consistently used IM networks as vectors for delivering phishing attempts, "poison URL's", and virus-laden file attachments from 2004 to the present, with over 1100 discrete attacks listed by the IM Security Center[5] in 2004-2007. Hackers use two methods of delivering malicious code through IM: delivery of virus, trojan, or spyware within an infected file, and the use of "socially engineered" text with a web address that entices the recipient to click on a URL that connects him or her to a website that then downloads malicious code. Viruses, worms, and trojans typically propagate by sending themselves rapidly through the infected user's buddy list. An effective attack using a poison URL may reach tens of thousands of people in minutes when each person's buddy list receives messages appearing to be from a trusted friend. The recipients click on the web address, and the entire cycle starts again. Infections may range from nuisance to criminal, and are becoming more sophisticated each year.
In addition to the malicious code threat, the use of instant messaging at work also creates a risk of non-compliance to laws and regulations governing the use of electronic communications in businesses. In the United States alone there are over 10,000 laws and regulations related to electronic messaging and records retention.[6] The more well-known of these include the Sarbanes-Oxley Act, HIPAA, and SEC 17a-3. Recent changes to Federal Rules of Civil Procedure, effective December 1, 2006, create a new category for electronic records which may be requested during discovery (law) in legal proceedings. Most countries around the world also regulate the use of electronic messaging and electronic records retention in similar fashion to the United States. The most common regulations related to IM at work involve the need to produce archived business communications to satisfy government or judicial requests under law. Many instant messaging communications fall into the category of business communications that must be archived and retrievable.
Organizations of all types must protect themselves from the liability of their employees' inappropriate use of IM. The informal, immediate, and ostensibly anonymous nature of instant messaging makes it a candidate for abuse in the workplace. The topic of inappropriate IM use became front page news in October 2006 when Congressman Mark Foley resigned his seat after admitting sending offensive instant messages of a sexual nature to underage former House pages from his Congressional office PC. The Mark Foley Scandal led to media coverage and mainstream newspaper articles warning of the risks of inappropriate IM use in workplaces. In most countries, corporations have a legal responsibility to ensure harassment-free work environment for employees. The use of corporate-owned computers, networks, and software to harass an individual or spread inappropriate jokes or language creates a liability for not only the offender but also the employer. A survey by IM archiving and security provider Akonix Systems, Inc. in March 2007 showed that 31% of respondents had been harassed over IM at work.[7] Companies now include instant messaging as an integral component of their policies on appropriate use of the World Wide Web, e-mail, and other corporate assets.







